Success Story: How a Pentest Protected a Logistics Company from Ransomware
Key highlights
Proactive security proves its value: Implemented security measures minimized the impact of a subsequent ransomware attack
Holistic security approach: From initial application pentest to complete infrastructure review and improvement process
Knowledge transfer and collaboration: Close cooperation with development and IT teams resulted in sustainable security improvements
Context
We have removed all details that could identify this company and have received permission to publish this story.
No business as usual
Our team began the pentest on the web application, focusing on common vulnerabilities such as SQL injections, cross-site scripting (XSS), and authentication weaknesses. During the test, we discovered an interesting vulnerability that not only gave us insights into the underlying workings of the application but also provided indicators about the backend server infrastructure. This was a so-called command injection vulnerability.
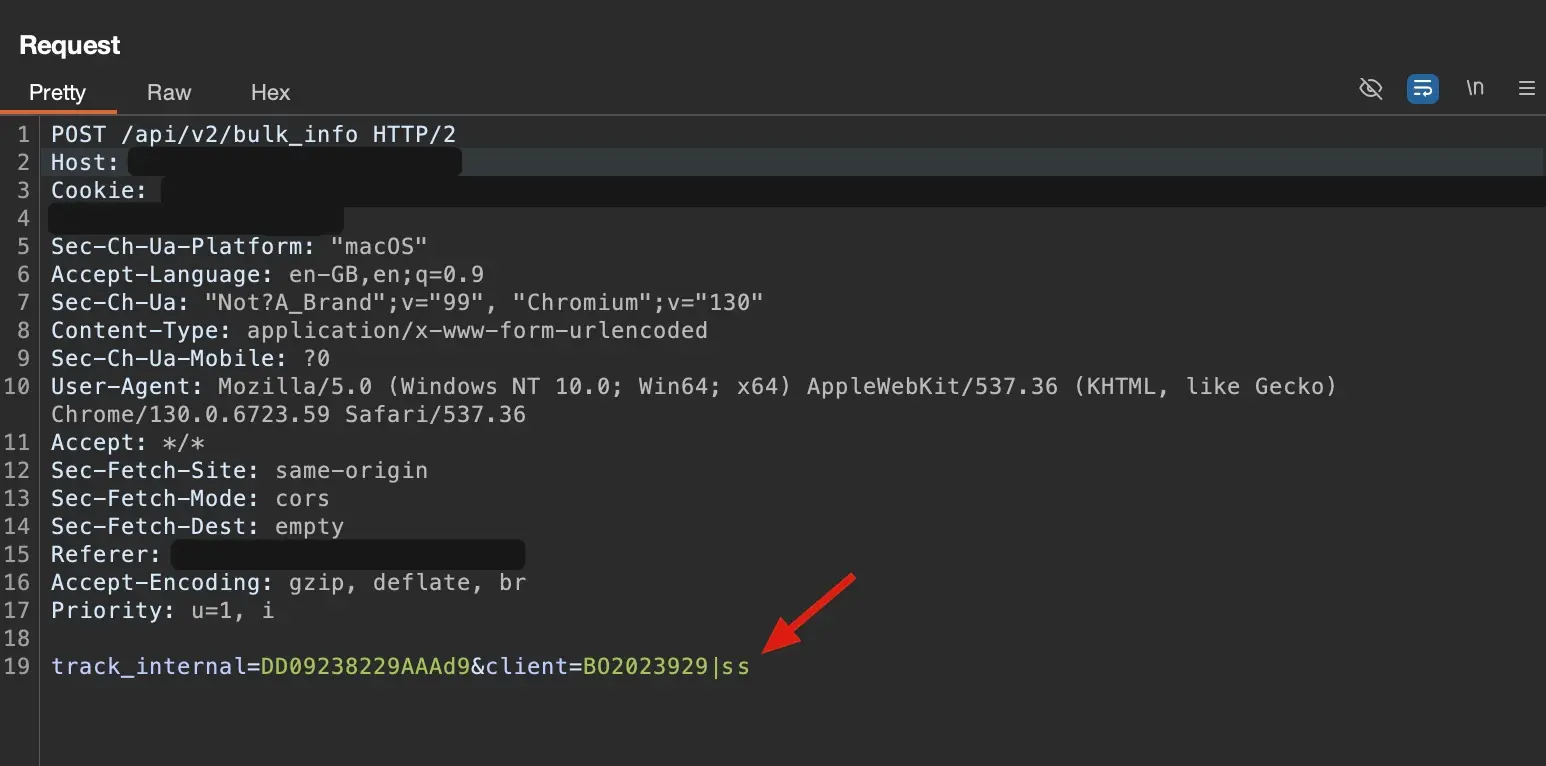
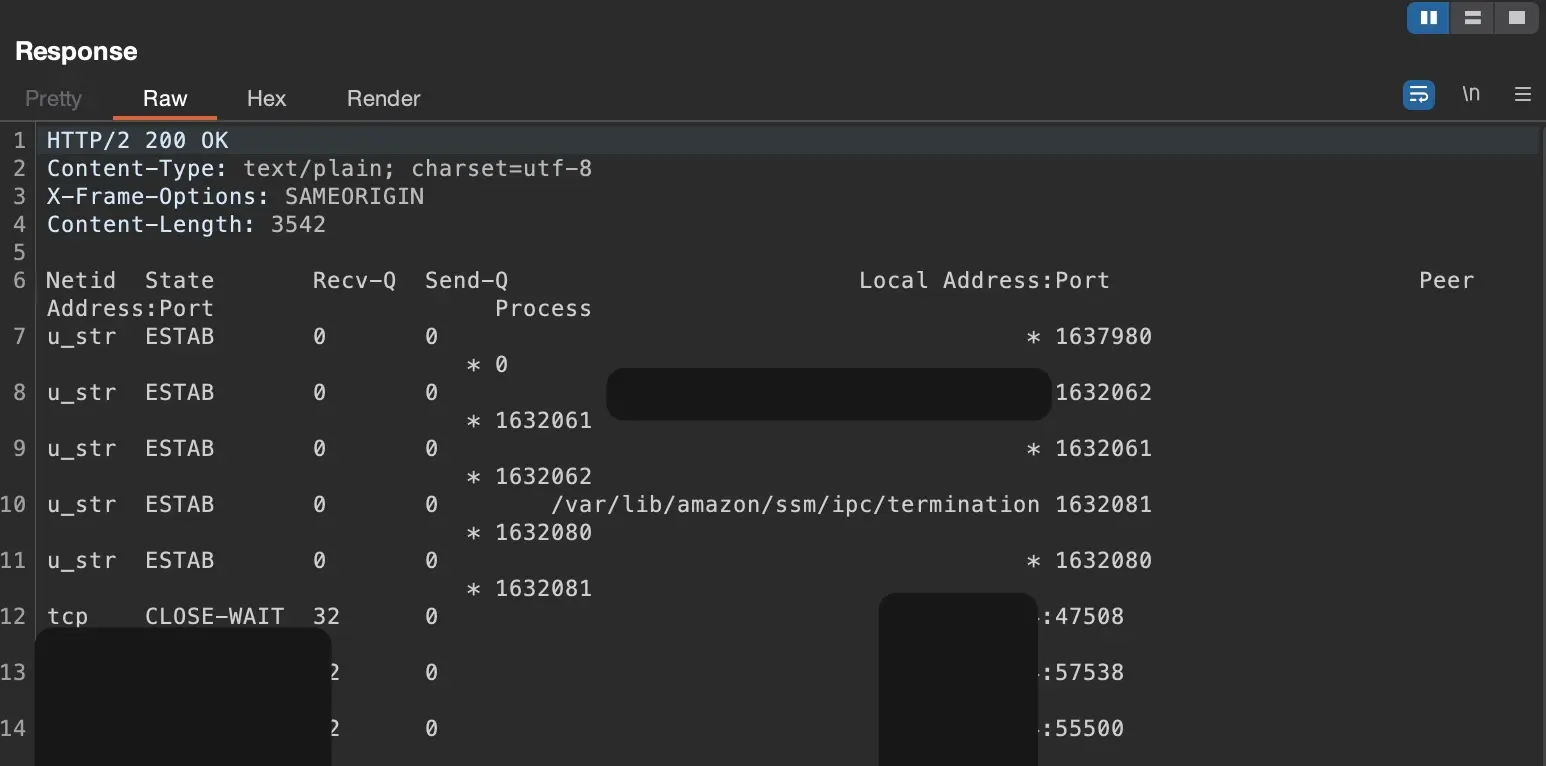
This meant that a malicious person could gain access not only to the application but also to sensitive customer data, logistics data, and API keys that were linked to other external parties.
All hands on deck
Server management revision: By using a different server management system, both the server patching problem and inventory management problem were solved. This made servers easier to update and maintained an current list of servers under management.
Segmentation and firewall security: Through several adjustments to the firewalls, individual servers were separated from each other with whitelisting on a need-to-be basis.
Monitoring and logging: Centralizing monitoring and logging to quickly detect suspicious activities.
Application patching: The development team received tips from us and a brief training to prevent future misconfigurations and make use of security frameworks to integrate into the application.
"Give a Man a Fish, and You Feed Him for a Day. Teach a Man To Fish, and You Feed Him for a Lifetime"
The ultimate test
Conclusion
